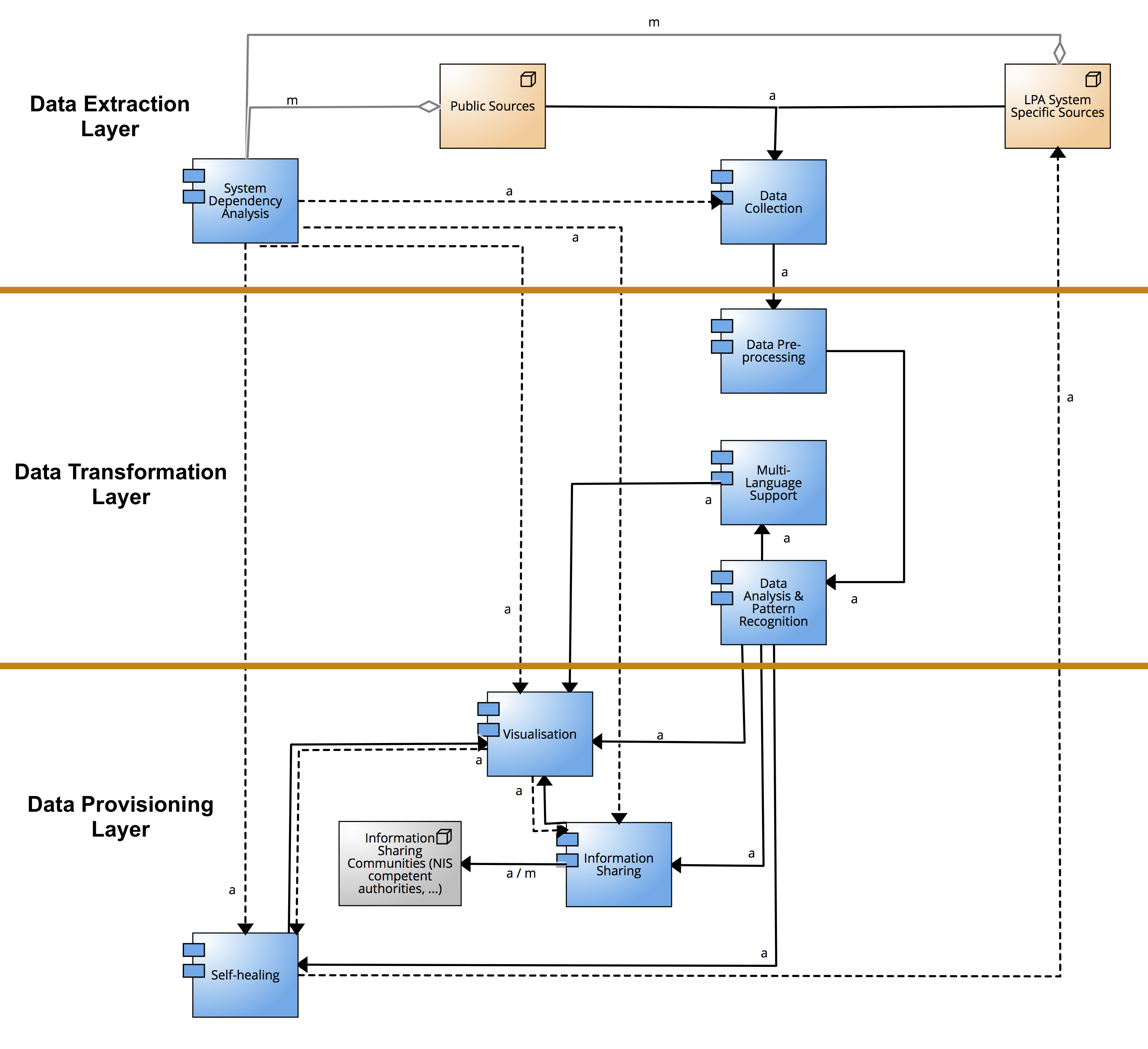
Cyber security, risk management and policies
Nowadays, organisations, ranging from banks and government agencies to SMEs, depend heavily on the management of risks in order to preserve their existence, operation and profitability. This appears to be undeniable since risks exist in various forms, such as information security, compliance, reputational and outsourcing risks. If those risks are not identified, assessed and mitigated [...]