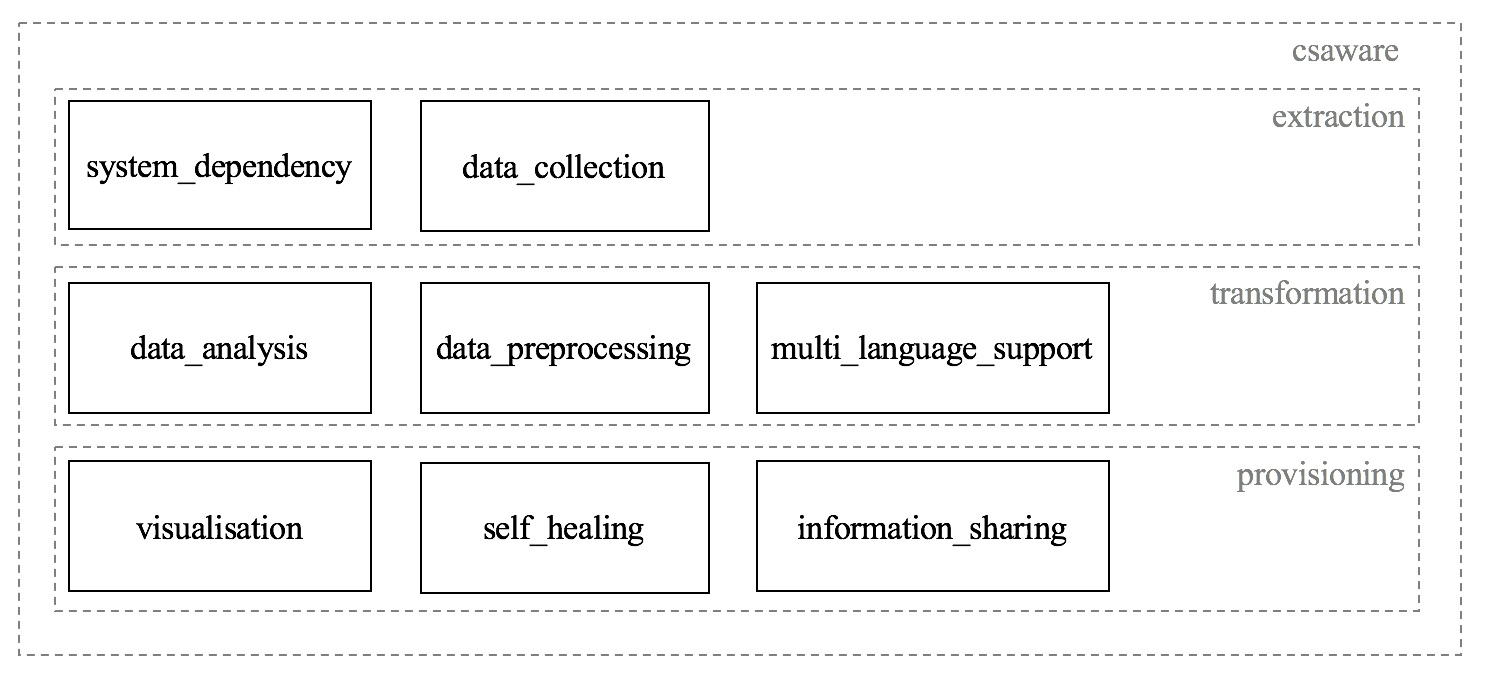
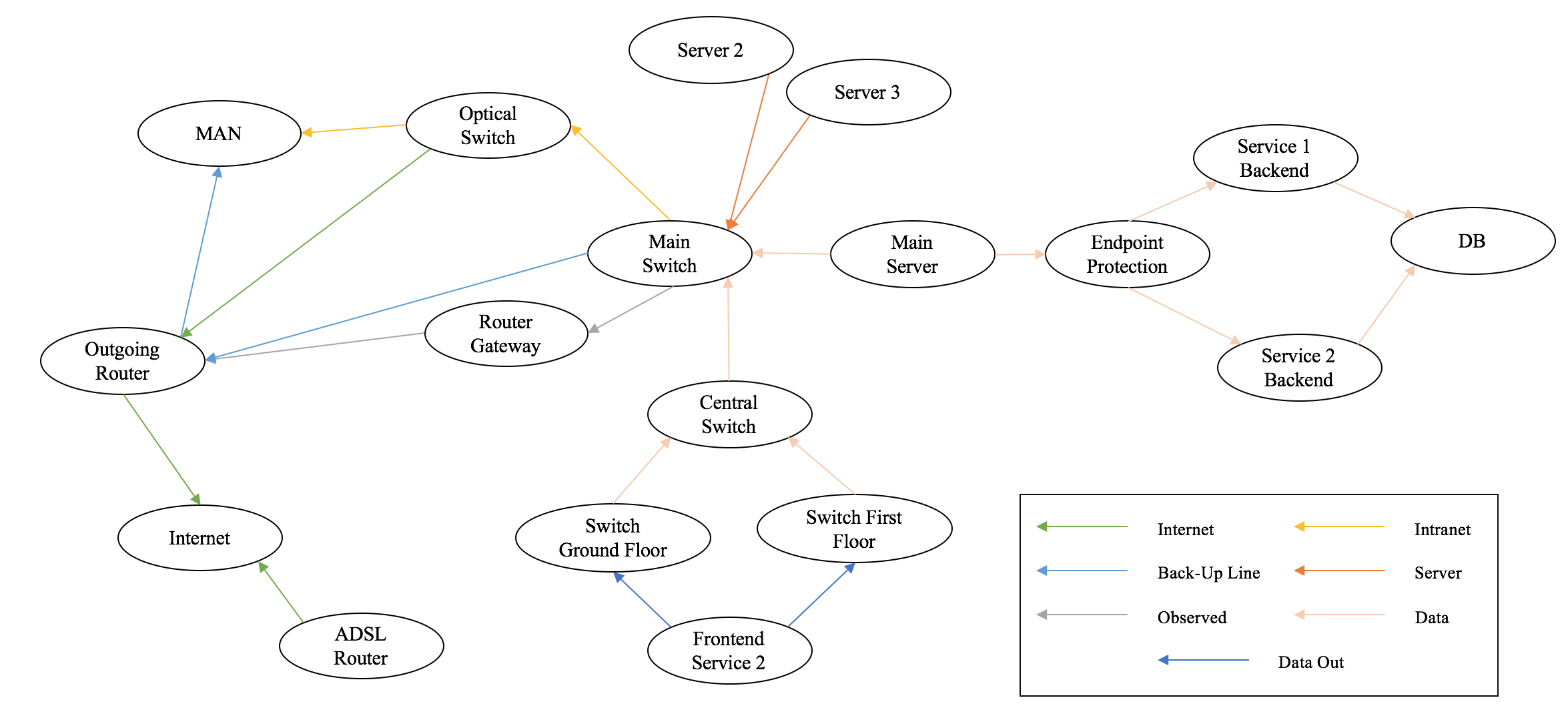
5G era and cybersecurity
Fifth-generation mobile networks or fifth-generation wireless systems, also known as “5G,” are the proposed next telecommunications standards and are likely to appear in the market in 2020. 5G networks are going to be very heterogeneous and complex compared to the current ones but in the same time are expected to meet high-end requirements. Among them, [...]