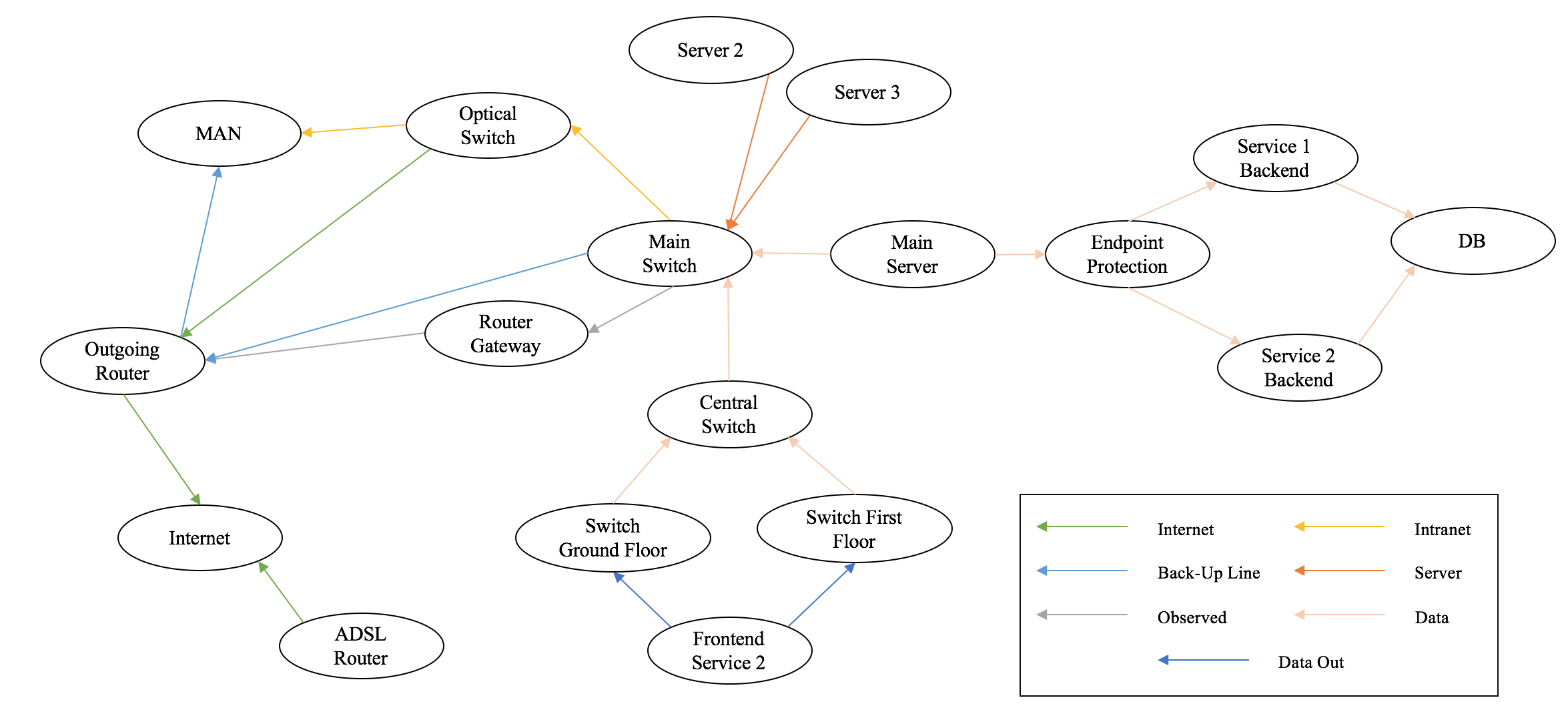
Biometrics technologies application for security
Biometrics technologies are nowadays emerging thanks to their potential applications in many different fields. Some examples are represented by the use of the fingerprint for mobile and laptop authentication and similarly, face recognition and iris scanning. Some of the aforementioned applications are very recent while the others are in use from some years. However, [...]